How Does a Blockchain Work?
A blockchain consists of programs called scripts that conduct the tasks you usually would in a database: Entering and accessing information and saving and storing it somewhere. A blockchain is distributed, which means multiple copies are saved on many machines, and they must all match for it to be valid.
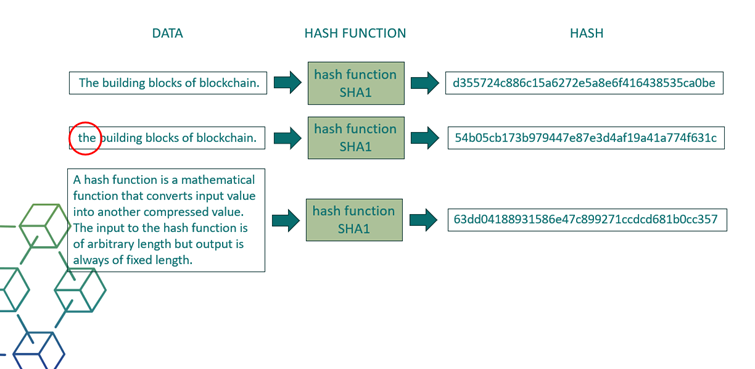
The blockchain collects transaction information and enters it into a block, like a cell in a spreadsheet containing information. Once it is full, the information is run through an encryption algorithm, which creates a hexadecimal number called the hash
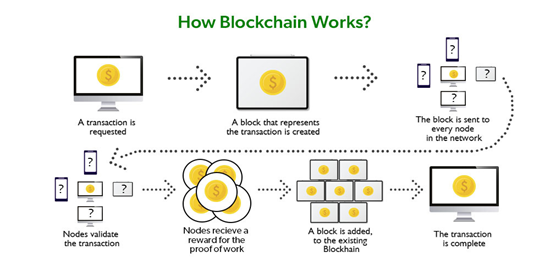
Figure 1 How the blockchain works (Source: https://www.geeksforgeeks.org/how-does-the-blockchain-work/ )
The transaction process in a blockchain can be summarized as follows:
The hash is then entered into the following block header and encrypted with the other information in the block. This creates a series of blocks that are chained together.
Transactions follow a specific process, depending on the blockchain they are taking place on. For example, on Bitcoin's blockchain, if you initiate a transaction using your cryptocurrency wallet—the application that provides an interface for the blockchain—it starts a sequence of events.
The traditional databases are centralized, mutable, and optimized for high-speed data processing, while blockchains are decentralized, immutable, and focused on providing trust and transparency through consensus mechanisms. The choice between the two depends on the specific needs of a given application.
Traditional Databases: Traditional databases are centralized systems where a single entity (e.g., a company or organization) has control over the database. They rely on a central server or a cluster of servers to manage and store data.
Blockchain: Blockchains are decentralized networks where data is distributed across multiple nodes (computers) in a network. There is no central authority or single point of control, making them resistant to censorship and tampering.
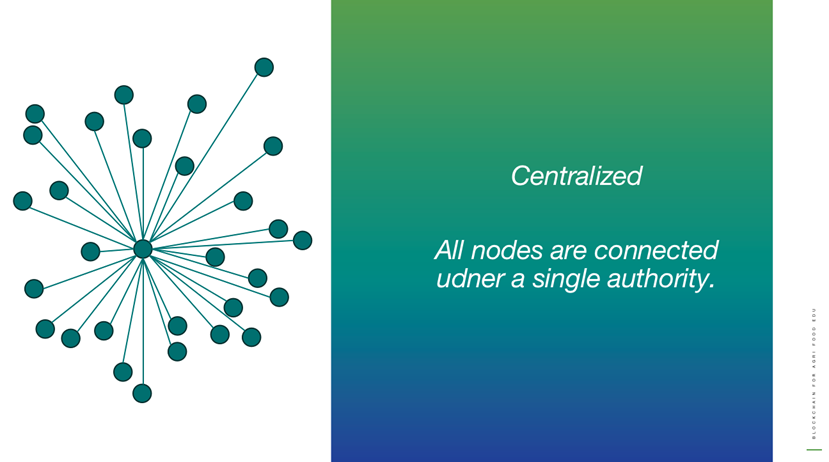
Centralized
All nodes are connected under a single authority.
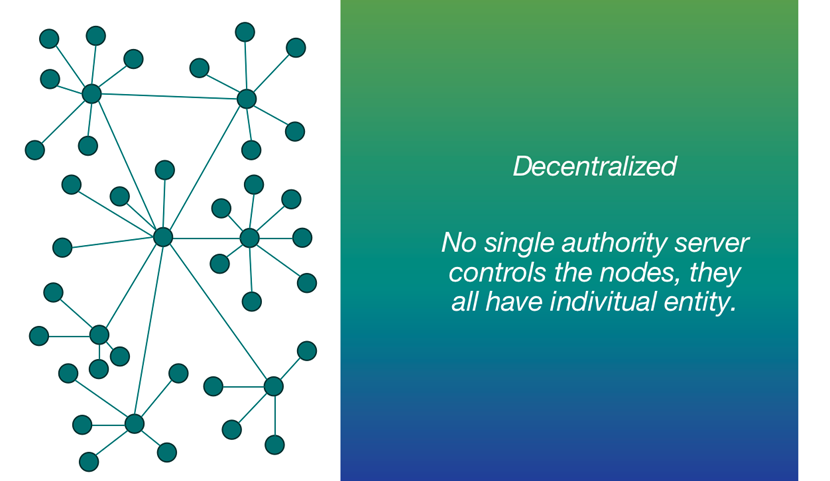
Decentralized
No single authority server controls the nodes, they all have individual entity.
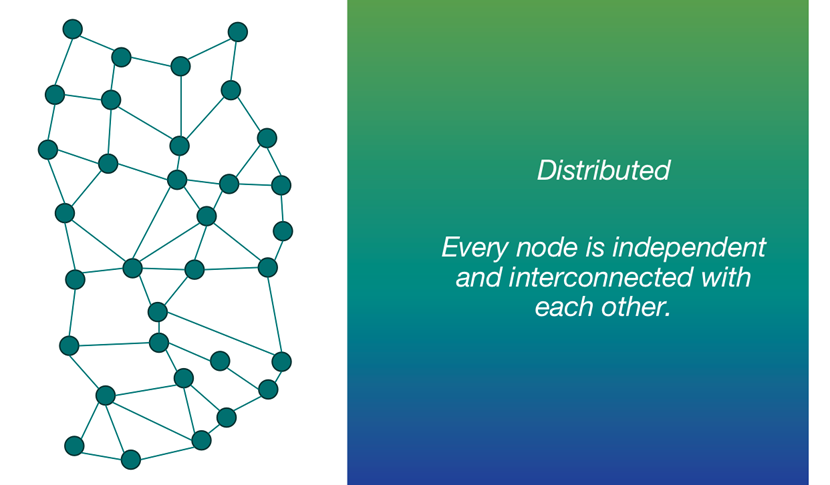
Distributed
Every node is independent and interconnected with each other.
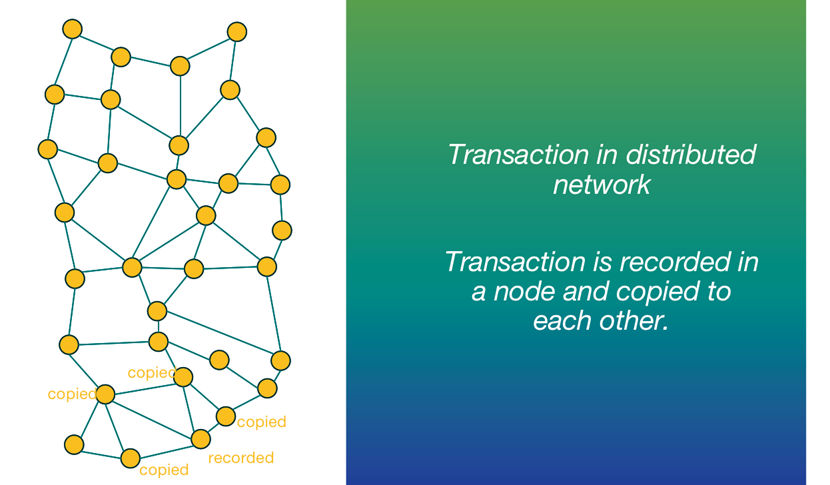
Transaction in distributed network
Transaction is recorded in a node and copied to each other.
A hash function is a mathematical function that converts input value into another compressed value. The input to the hash function is of arbitrary length but output is always of fixed length.
Hash functions are extremely useful and appear in almost all information security applications.
This property means that it should be computationally hard to reverse a hash function.
In other words, if a hash function h produced a hash value z, then it should be a difficult process to find any input value x that hashes to z.
This property protects against an attacker who only has a hash value and is trying to find the input.
This property means it should be hard to find two different inputs of any length that result in the same hash. This property is also referred to as collision free hash function.
In other words, for a hash function h, it is hard to find any two different inputs x and y such that h(x) = h(y).
Since, hash function is compressing function with fixed hash length, it is impossible for a hash function not to have collisions. This property of collision free only confirms that these collisions should be hard to find.
This property makes it very difficult for an attacker to find two input values with the same hash.
Also, if a hash function is collision-resistant then it is second pre-image resistant.
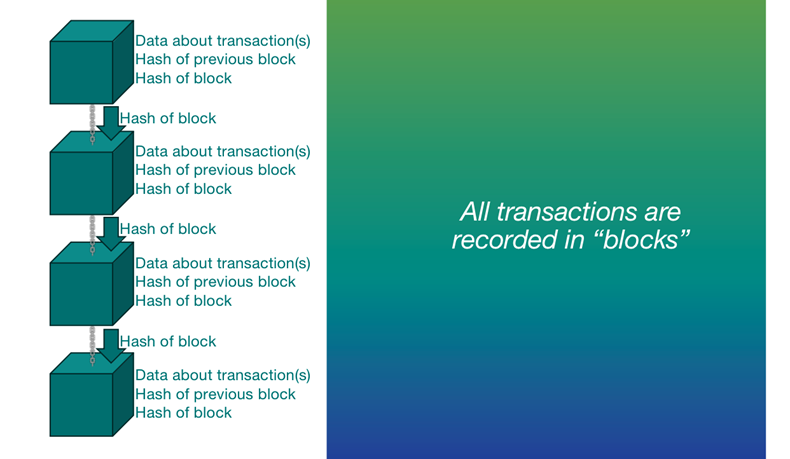
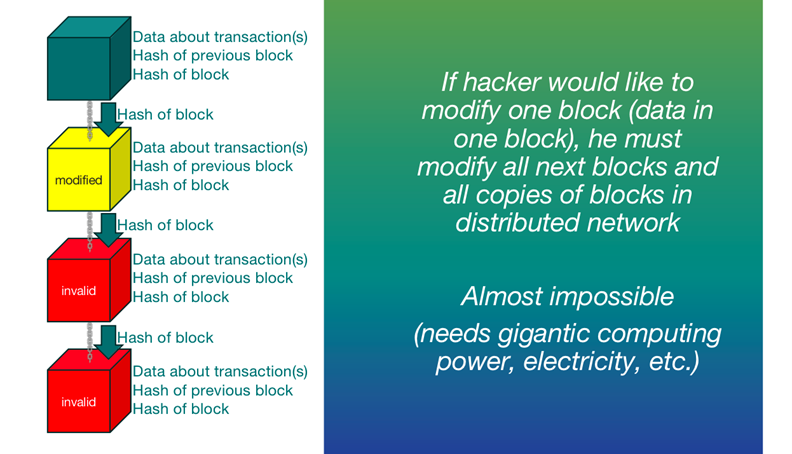
Block = data + hash of previous block + hash
Chain = chain between blocks
Proof of work (PoW) is a form of cryptographic proof in which one party (the prover) proves to others (the verifiers) that a certain amount of a specific computational effort has been expended.
Verifiers can subsequently confirm this expenditure with minimal effort on their part.
Proof-of-stake (PoS) protocols are a class of consensus mechanisms for blockchains that work by selecting validators in proportion to their quantity of holdings in the associated cryptocurrency.
This is done to avoid the computational cost of proof-of-work (POW) schemes.
Traditional Databases: Traditional databases use tables to organize data in a structured manner, typically following a predefined schema.
Blockchain: Blockchains use a ledger structure where data is organized into blocks, and each block contains a list of transactions or data entries. The structure is typically less rigid, allowing for more flexibility in data types and formats.
Traditional Databases: Access control is managed by a centralized authority, and permissions can be granted or revoked for various users or roles.
Blockchain: Access control is often managed through cryptographic keys. Users have control over their private keys, allowing them to interact with the blockchain without relying on a central authority. Public blockchains are typically permissionless, while private blockchains may have varying levels of access control.
Traditional Databases: Traditional databases do not rely on a consensus mechanism among multiple parties. They assume that the data stored in the database is accurate.
Blockchain: Blockchains use consensus mechanisms (e.g., Proof of Work, Proof of Stake) to validate and agree on the state of the ledger. This ensures that all participants in the network have a shared and agreed-upon view of the data.
Traditional Databases: Data in traditional databases can be modified or deleted by authorized users with the necessary permissions.
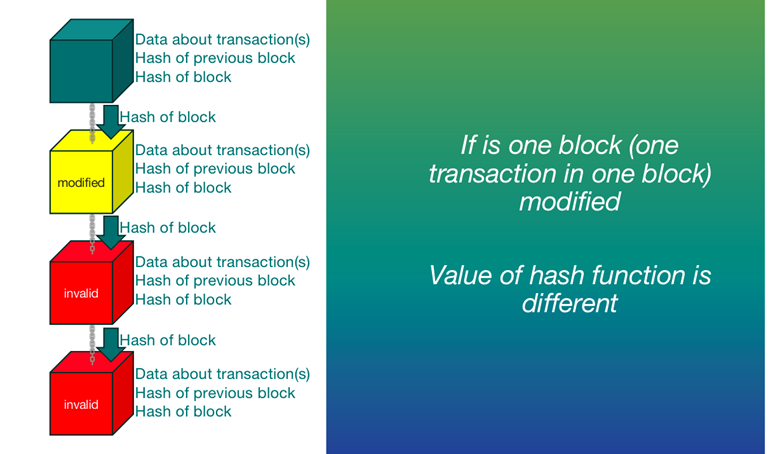
Blockchain: Once data is recorded on the blockchain, it is typically immutable and resistant to alteration. This immutability is a core feature of blockchain technology.
Traditional Databases: Traditional databases are often optimized for high transaction speeds and can scale easily by adding more servers or resources.
Blockchain: Public blockchains, especially those using Proof of Work, can have slower transaction processing speeds and scalability challenges. However, various solutions and technologies are being developed to improve blockchain scalability.
Traditional Databases: Traditional databases are well-suited for applications that require high throughput, low latency, and centralized control, such as banking systems and e-commerce platforms.
Blockchain: Blockchains are best suited for applications requiring decentralization, trust, transparency, and security, such as cryptocurrencies, supply chain tracking, voting systems, and smart contracts.